PicoCTF: Wireshark Doo Doo / Wireshark Two two
(Digital Forensics and packet analysis with .pcapng files)
The challenge can be found here in the PicoCTF Forensics category. The flag will not be posted at the end of this writeup, but the steps are provided below for how to reach it.
WIRESHARK DOO DOO:
Under the description of the challenge, a .pcapng file is given. PCAPNG files are recorded network traffic that can be analyzed with a program like Wireshark. After opening the file in Wireshark, there is a chaotic amount of data packed into the file.
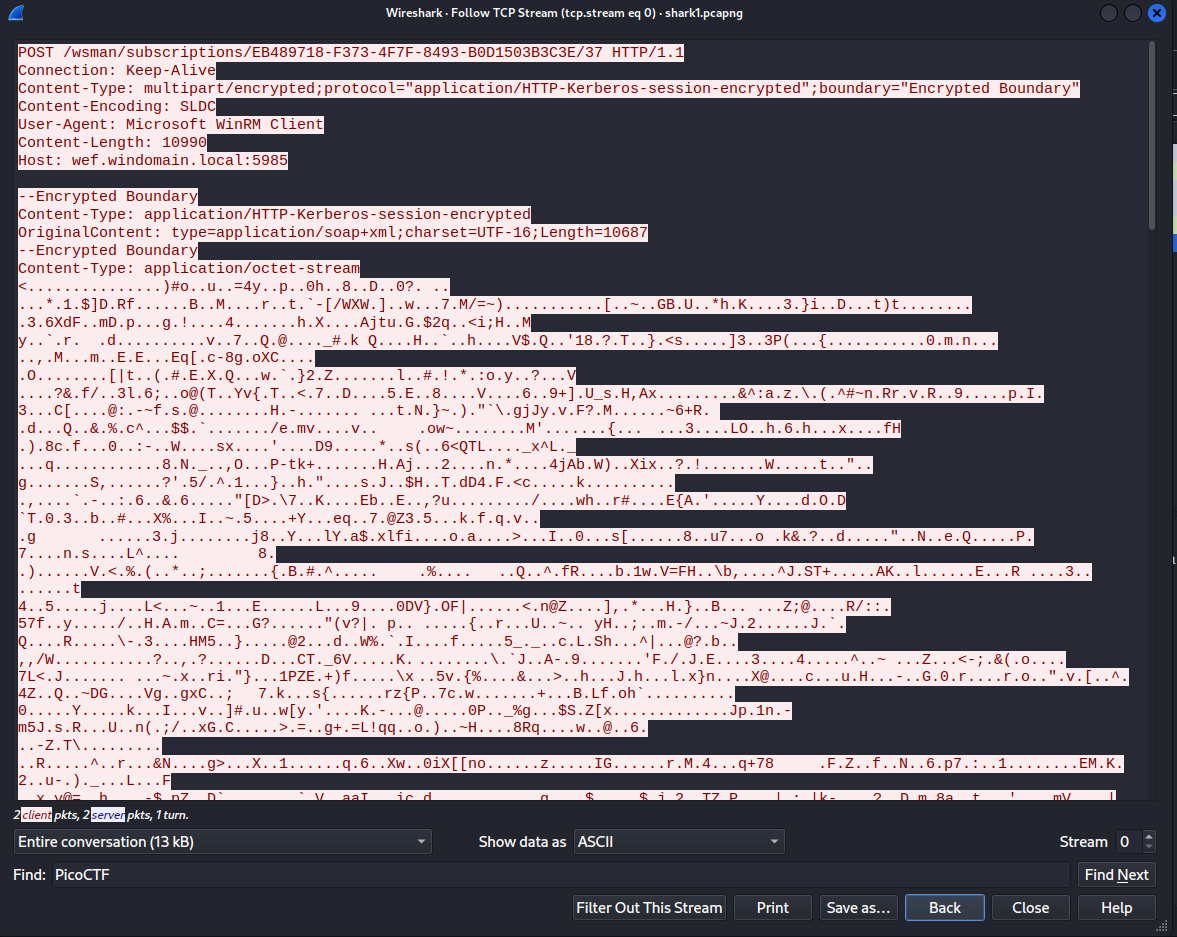
In order to make everything easier to read, it can be worthwhile to follow the TCP Stream.
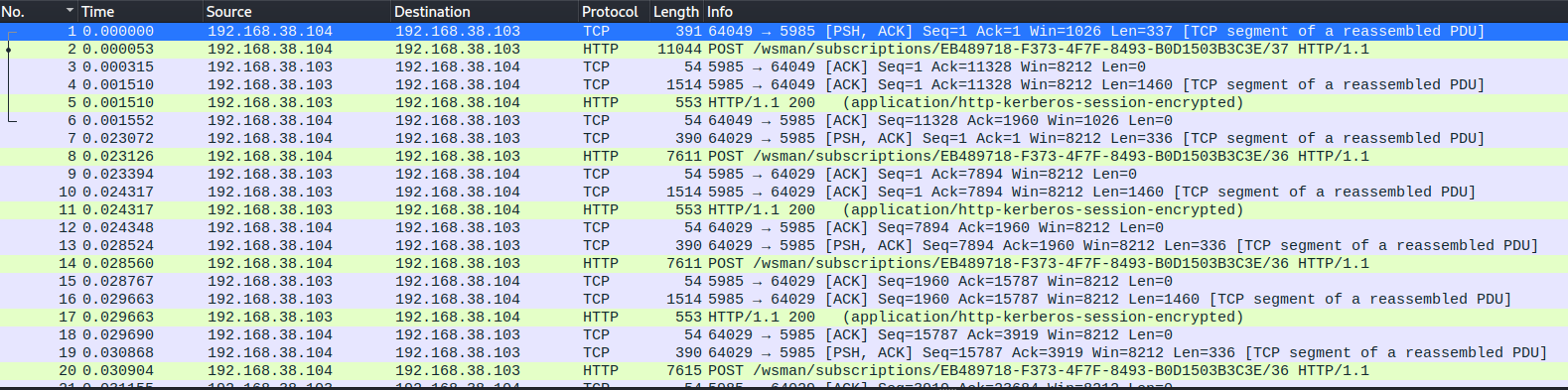
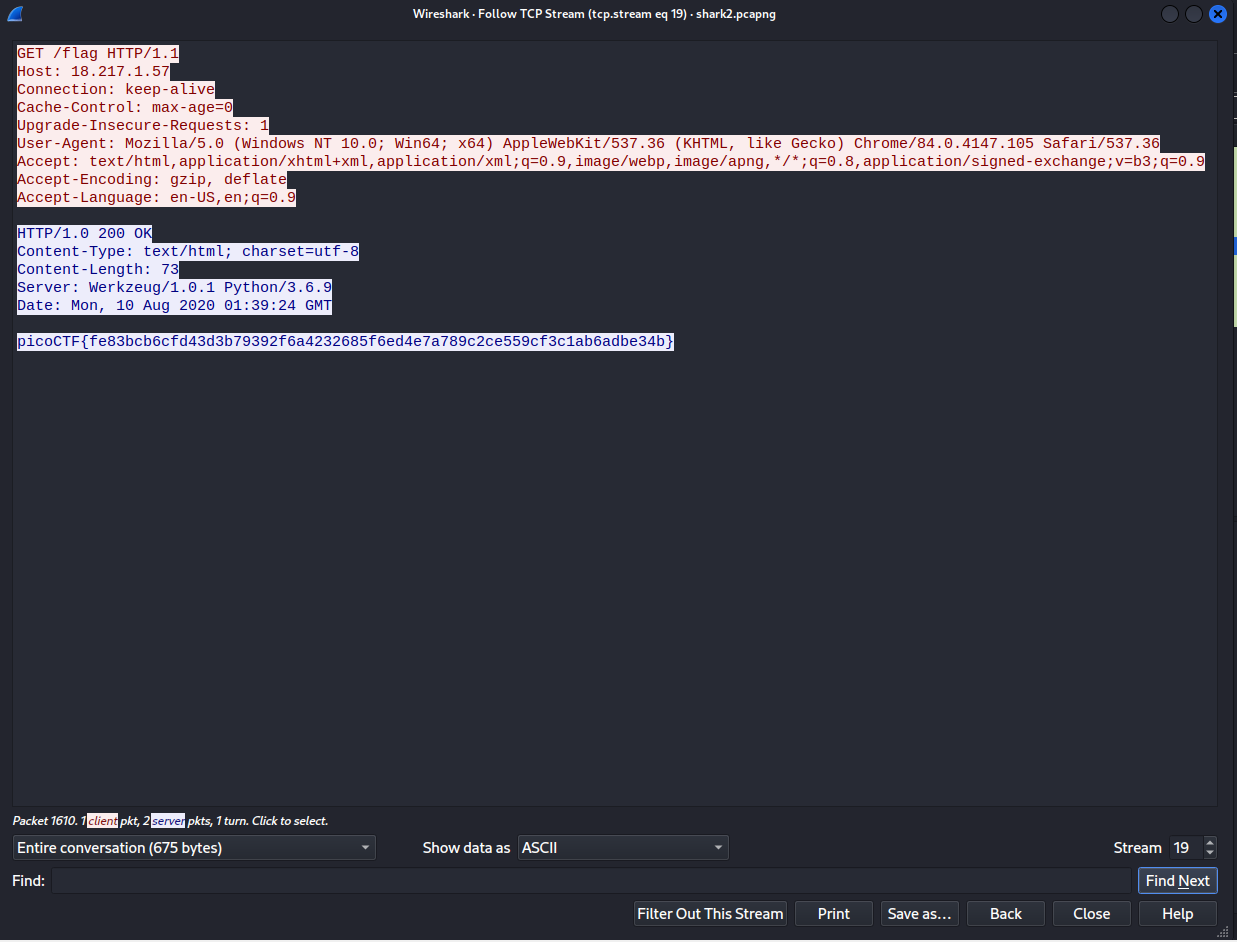
When following the TCP stream, a display filter is applied that isolates the data from each individual stream. When quickly scanning through the streams (using the arrows at the bottom right), Stream 5 stands out.
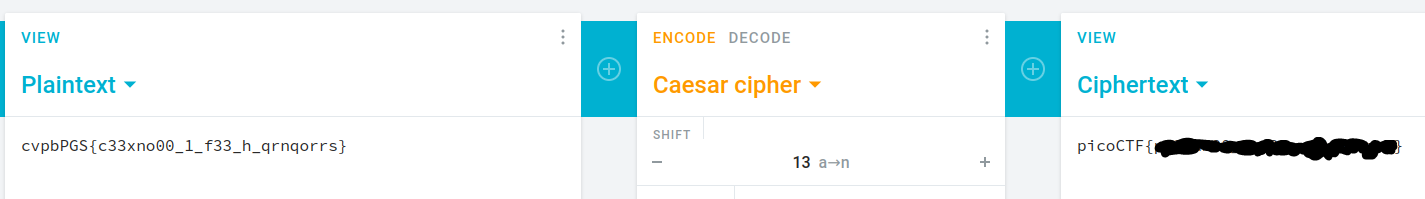
The string at the bottom of Stream 5 is in the same format as the flag. It is most likely not encoded as the brackets are still in place within the string. Placing the string into a Caesar cipher is a good place to start when trying to figure out how to decode the text.
Each character in the string is shifted by 13; once the string entered into the cipher, the output will be the flag.
Wireshark Two Two:
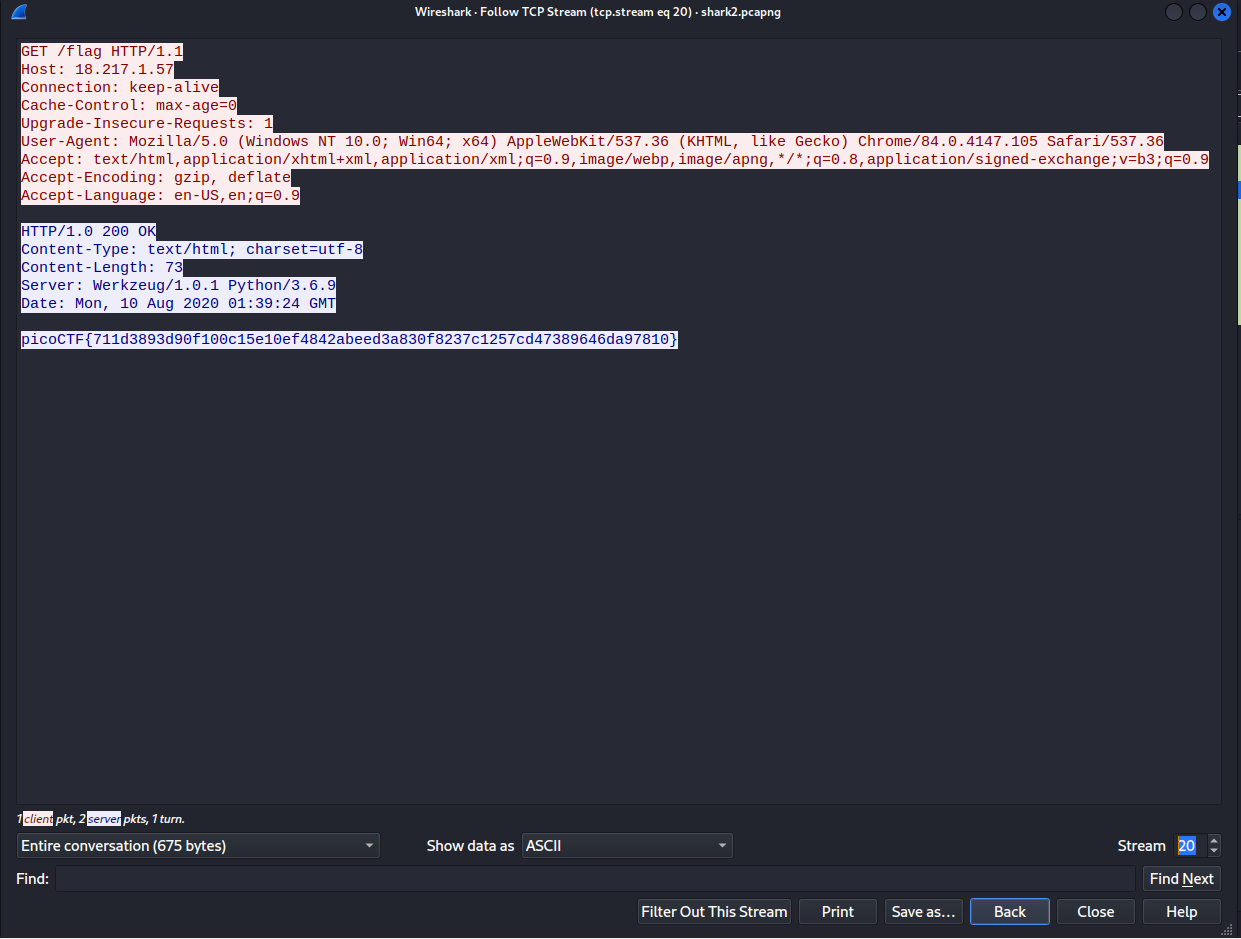
Similar to the previous challenge, download the file and open it in Wireshark. When checking the TCP Streams, there are many of what appear to be “flags” spread out through them.
The strings inside the brackets of these "flags" look like they could be either hashes or hexadecimal; however, when these strings are checked, they return nothing. When attempting to decode the strings ends in a dead end, it is apparent that something has been overlooked in the initial data dump of the file.
Upon going back to Wireshark, enter the display filter of "tcp.stream eq 19" to see the traffic for the TCP Stream in which the first “flag” was seen. There is no useful TCP data, so it is worth trying to change the filter to see what other data has been captured. After changing the filter to "udp.stream eq 19", there is a request to a domain named "ky0+eTqU.reddshrimpandherring.com". The words "red” and “herring" confirm the idea that the TCP Streams are nothing more than a decoy intent on wasting time.
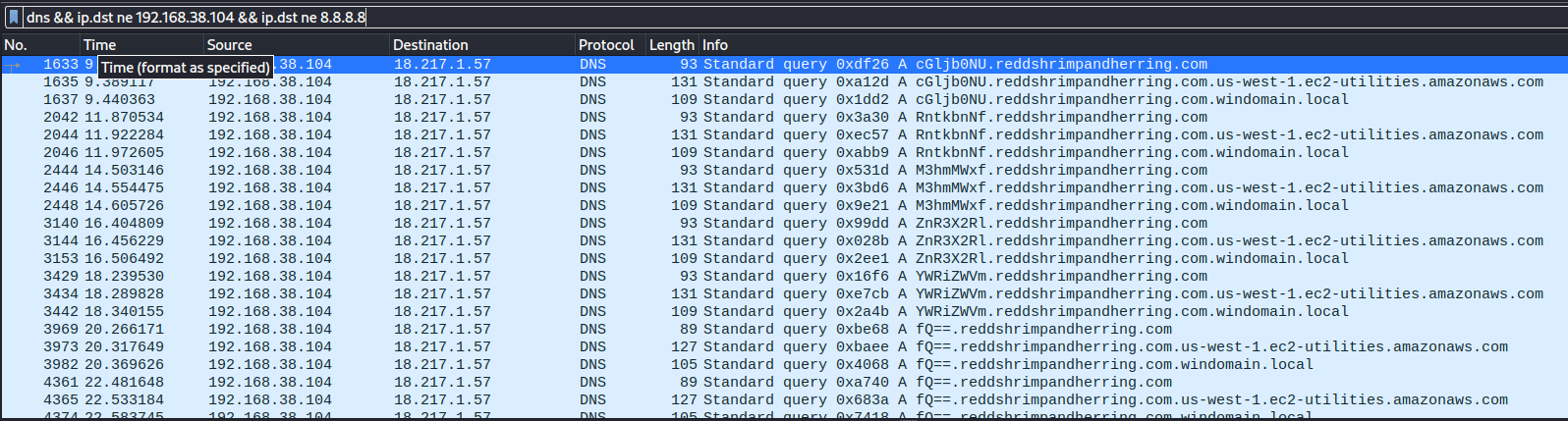
Applying a new filter "dns" to the capture reveals an excessive amount of DNS traffic through two main IP addresses, "192.168.38.104" and "8.8.8.8".
These two IP addresses can be filtered using "dns && ip.dst ne 192.168.38.104 && ip.dst ne 8.8.8.8". The "ne" within the filter signifies to only reveal the IP addresses that are Not Equal to the two previously mentioned addresses.
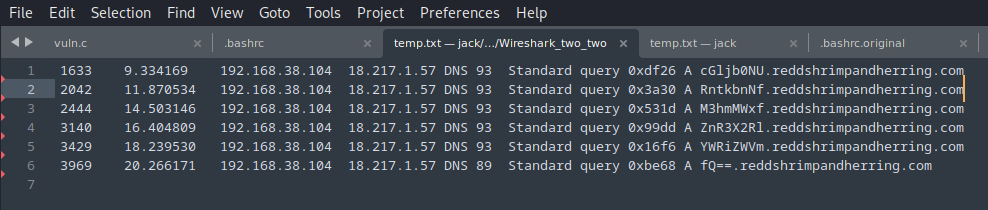
After applying this filter, there is only one IP address remaining. In addition to this, the resulting DNS names look suspicious. The prefix of each of them looks as though it could be part of a Base64 string because of the two "=" at the end of the last prefix. Since there is not much data to deal with here, it is easiest to copy and paste the remaining results into a text file, deleting any duplicate DNS names, so that it can be parsed and decoded from Base64.
The final task is writing a command to parse the text within the file and decode the results from Base64. Awk can be used in this case as the lines are all similar with the same column of data needing to be extracted. Once the specific lines are parsed from the original file, the first column until the period can be taken out of the text, allowing the Base64 chunks to be parsed from the domain name. Finally, these Base64 chunks can have the newlines removed by using the "tr" command, giving a single string of text to decode from Base64.
awk '{print $11}' temp.txt | awk -F. '{print $1}' | tr -d '\n' | base64 -d
After running this command, the flag is the output.